
Managing access control at a fine-grained level is a must-have for modern applications, but it's also one of the most challenging tasks in software engineering. Designing and implementing a robust, flexible, and scalable authorization system is a challenge many developers face. However, there are solutions to this problem: permission systems based on Google Zanzibar paper, such as SpiceDB. In this blog post, I will show you how to model an authorization system in SpiceDB, using Google Drive as an example.
Contents
- Step 1. Describe the requirements
- Step 2. Define resources
- Step 3. Define subjects
- Step 4. Define relations
- Step 5. Define permissions
- Step 6. Verify the model
Step 1. Describe the requirements
The first step towards building an authorization system is to describe the requirements in plain language. Try to make the sentences look like this:
As a subject, I can permission a resource if relations.
For example, we can define the Google Drive requirements as follows:
- A user or a group member can view a document if they are the owner, viewer, commenter, or editor or if they can view documents in the parent folder.
- A user or a group member can edit a document if they are the owner or editor or if they can edit documents in the parent folder.
- A user or a group member can comment on a document if they are the owner, editor, or commenter or if they can comment on documents in the parent folder.
- A user can create a document in a folder if they are the owner of the folder or if they can create a document in the parent folder.
- A user can delete a document if they are the owner or if they can delete documents in the parent folder.
- A user can share a document if they are the owner or if they can share documents in the parent folder.
Step 2. Define resources
The next step is to define the resources and their relations. Resources are the objects that the subjects can access. In Google Drive, we have two primary resources: folders and documents. Both of them might have a parent folder.
Step 3. Define subjects
The subjects are the objects that can access the resources. In Google Drive, you can access a folder or a document by having explicit permission or being a group member.
Step 4. Define relations
Once we have the resources and subjects identified, we can connect them using relations. The relations will be used to finally build the permissions in the next step. You can think about relations as roles. For example, in our Google Drive example, we can define 4 relations in file and document resources:
- Owner
- Viewer
- Commenter
- Editor
Each relation can be assigned to either a user or a group. We can use subject relations to grant a role to all group members.
Step 5. Define permissions
Now, we can use the relations to define the permissions. A rule of thumb is to have one permission for each API or action. For our example, let's define the following permissions:
- View
- Edit
- Comment
- Share
- Delete
As the viewer of the parent folder should have access to all descendant documents, we are using the recursive permissions.
Step 6. Verify the model
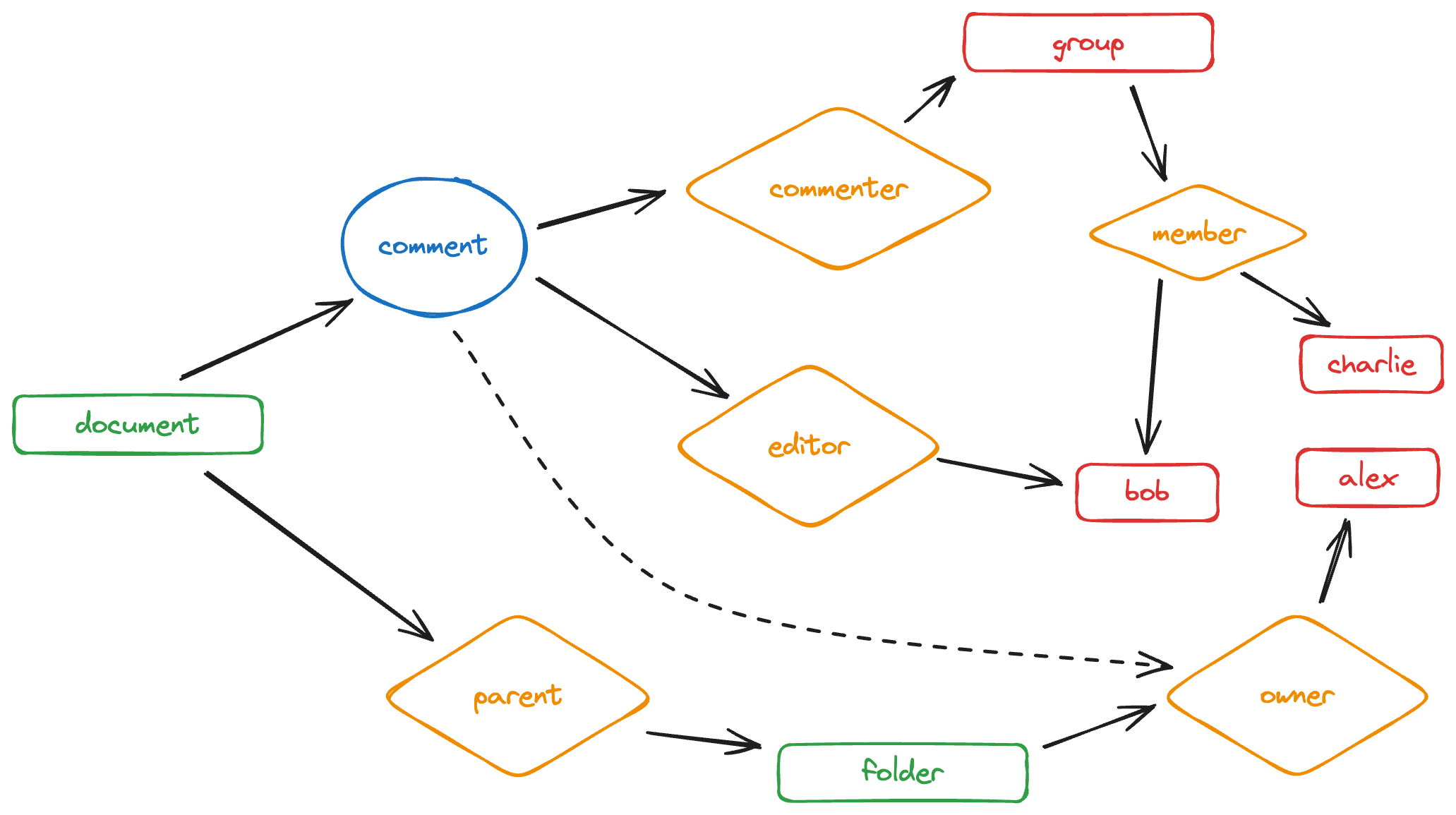
The final step is to verify the model on some test data. Here is the overview of our test case:
- The parent is the parent folder of the document document.
- Alex is the owner of the parent folder.
- Bob is the editor of the document file.
- Charlie is the viewer of the document file.
- Bob and Charlie are members of the group.
- The group members are commenters on the document file.
Running the expected relations on this test data gives the following results:
The following diagram visualizes who can comment on a document and why.
You can see the entire schema, with test relationships and expected relations, at https://play.authzed.com/s/yx7vtTs8YIvN/schema.